Configuring HTTPS
Configure a reverse proxy to allow clients to access Tamr Core securely over HTTPS.
Configure the NGINX reverse proxy server to allow clients to access Tamr Core securely over HTTPS. Tamr Core requires only one port to be reachable from the client. By default this port is 9100. NGINX configuration establishes a proxy between the default Tamr Core port 9100 on HTTP and port 443 on HTTPS. The proxy allows:
- The client and NGINX proxy to communicate over HTTPS.
- NGINX proxy and Tamr Core server to communicate over HTTP.
Note: If you plan to forward HTTP traffic to HTTPS, also open port 80.
When configuring NGINX, you further secure your deployment by configuring secure cookies and disabling caching.
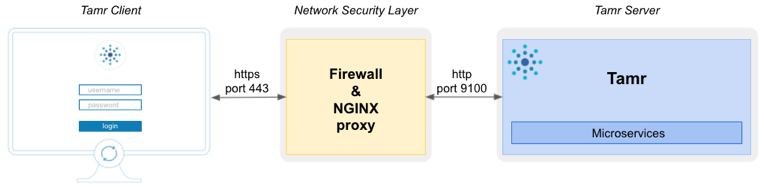
To access Tamr Core securely over HTTPS, use a reverse proxy.
For a list of additional ports that Tamr Core and its dependencies use, see Included Services and Ports. These ports are used for internal communications and do not need to be served to the client.
Before You Begin:
- Configure the firewall for the deployment to allow client traffic to enter on port
443. If you plan to forward HTTP traffic to HTTPS, also open port80. See Single-Node Deployments, Deploying Tamr on AWS, Deploying Tamr on Azure, or Deploying Tamr on Google Cloud Platform. - Install NGINX.
NGINX Default Limits
NGINX has the following default limits for uploading files and header size:
- The default file size limit for uploading files through NGINX is 1MB. If the default is left unchanged, you can only upload files to Tamr Core via HTTPS that are up to 1MB in size. This limit does not apply to clients uploading files via HTTP, such as clients acting locally on the Tamr Core server.
In the examples that follow,client_max_body_sizeis set to0to allow for uploading large datasets. If you need to place a limit on file sizes, remove that line from the configuration or set it to a value such as 10M. - If using SPNEGO and Kerberos authentication, the default limits on the header buffer number and size,
4 8k, are too small to allow the keytab value to pass, and a414 (Request-URI Too Large)exception will be thrown.
Configure the propertylarge_client_header_buffersto set the maximum number and size of buffers used for reading large client request headers, such as4 16k.
Configuring an NGINX server proxy for HTTPS
Configuring an NGINX server proxy for HTTPS allows you to have a secure access to Tamr Core over HTTPS. This topic describes the following approaches for configuring the server proxy for HTTPS:
- Using a certificate and optional passphrase.
- Using a certificate signing request and privacy-enhanced mail.
Before You Begin:
Plan to work with your IT team to generate a certificate and key from a valid certification authority (CA). Self-signed certificates might not work in your environment, and your browser might not trust them.
- Obtain a signed certificate
.crtfile. - Obtain the signed certificate's private key
.keyfile. - (Optional) Obtain the passphrase.
Configuring an NGINX Server Proxy for HTTPS Using a Certificate and (Optional) Pass Phrase
Follow the steps in this procedure to configure HTTPS, configure secure cookies, and disable caching.
To configure NGINX for HTTPS using a certificate and passphrase:
- Copy the certificate
.crtand private key.keyfiles into a directory, such as/etc/nginx/keys:
sudo mkdir /etc/nginx/keys
cd /etc/nginx/keys
sudo cp <signed-certificate>.crt .
sudo cp <signed-certificate-private-key>.key .
- (Optional) Create a passphrase file to store the private key's passphrase:
cd /etc/nginx/keys
sudo vi global.pass
- In the NGINX configuration directory
/etc/nginx/conf.d, create the configuration filetamr.conf:
cd /etc/nginx/conf.d
vi tamr.conf
- In the
tamr.conffile, add the following configuration. If you are not using a passphrase, omitssl_password_file /etc/nginx/keys/global.pass;.
Note: The following example includes a setting for proxy_cookie_flags. To use this feature, v1.19.3 or later of NGINX is required.
server {
# Full path to the file containing the passphrase.
ssl_password_file /etc/nginx/keys/global.pass;
# SSL configuration
listen 443 ssl default_server;
listen [::]:443 ssl default_server;
root /var/www/html;
# Add index.php to the list if you are using PHP
index index.html index.htm index.nginx-debian.html;
server_name _;
ssl_certificate /etc/nginx/keys/<signed-certificate>.crt;
ssl_certificate_key /etc/nginx/keys/<signed-certificate-private-key>.key;
ssl_session_cache builtin:1000 shared:SSL:10m;
ssl_protocols TLSv1.2;
ssl_ciphers HIGH:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4;
ssl_prefer_server_ciphers on;
# do not limit file upload size
client_max_body_size 0;
location / {
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_pass http://localhost:9100;
proxy_read_timeout 3600;
proxy_redirect http://localhost:9100 https://localhost:443;
# Disable caching
proxy_hide_header Cache-Control;
add_header Cache-Control "no-store";
# Mark cookies as secure
proxy_cookie_flags ~ secure samesite=strict;
}
}
- Restart the NGINX service:
sudo systemctl restart nginx.service
- Confirm that Tamr Core is now available by browsing directly to
https://<hostname>:443, such ashttps://tamr.<mydomain>.com.
Configuring an NGINX Server Proxy for HTTPS Using a Certificate Signing Request and Privacy-Enhanced Mail
Follow the steps in this procedure to configure HTTPS, configure secure cookies, and disable caching.
To configure NGINX for HTTPS using a certificate signing request and privacy-enhanced mail:
- Generate a certificate signing request,
.csrand private key,.key, and enter the required domain details when prompted:
openssl req -new -newkey rsa:2048 -nodes -keyout <domain-name>.key -out <domain-name>.csr
- Send the
.csrfile to the security team in charge of the server, who will be able to provide the privacy-enhanced mail file,.crt. - Copy the certificate signing request, privacy-enhanced mail and private key files,
.csr,.crt, and.keyrespectively, into a directory, such as/etc/nginx/keys:
sudo mkdir /etc/nginx/keys
cd /etc/nginx/keys
sudo cp <certificate-signing-request>.csr .
sudo cp <privacy-enhanced-mail>.crt .
sudo cp <certificate-private-key>.key .
- In the NGINX configuration directory
/etc/nginx/conf.d, create the configuration filetamr.conf:
cd /etc/nginx/conf.d
vi tamr.conf
- In the
tamr.conffile, add the following configuration:
server {
# SSL configuration
listen 443 ssl default_server;
listen [::]:443 ssl default_server;
root /var/www/html;
# Add index.php to the list if you are using PHP
index index.html index.htm index.nginx-debian.html;
server_name _;
ssl_certificate /etc/nginx/keys/<signed-certificate>.crt;
ssl_certificate_key /etc/nginx/keys/<signed-certificate-private-key>.key;
ssl_session_cache builtin:1000 shared:SSL:10m;
ssl_protocols TLSv1.2;
ssl_ciphers HIGH:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4;
ssl_prefer_server_ciphers on;
# do not limit file upload size
client_max_body_size 0;
location / {
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_pass http://localhost:9100;
proxy_read_timeout 3600;
proxy_redirect http://localhost:9100 https://localhost:443;
# Disable caching
proxy_hide_header Cache-Control;
add_header Cache-Control "no-store";
# Mark cookies as secure
proxy_cookie_flags ~ secure samesite=strict;
}
}
- Restart the NGINX service:
sudo systemctl restart nginx.service
- Confirm that Tamr Core is now available by browsing directly to
https://<hostname>:443, such ashttps://tamr.<mydomain>.com.
Optional: Set NGINX X-Content-Type-Options to “nosniff”
MIME type sniffing is a standard functionality in browsers to identify an appropriate way to render data when the HTTP headers sent by the server are either inconclusive or missing.
You can configure NGINX to instruct the browser to trust that the site has sent the appropriate content-type, and block MIME-sniffing on the response body.
In the NGINX configuration file at /etc/nginx/nginx.conf file, add the following configuration:
add_header X-Content-Type-Options nosniff;.
Updated over 1 year ago