HTTPS
Configure a reverse proxy through NGINX to allow clients to access Tamr securely over HTTPS.
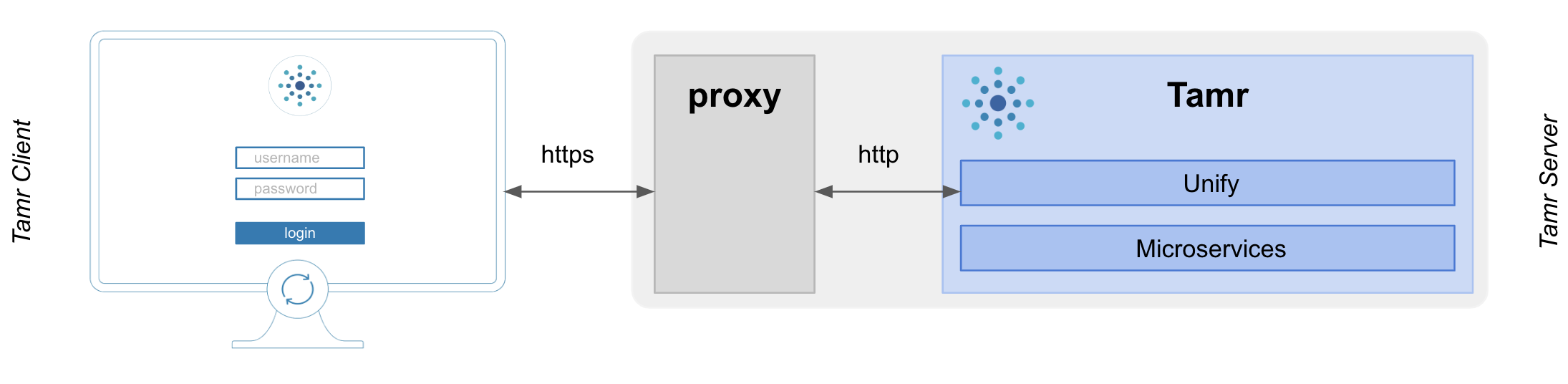
To access Tamr securely over HTTPS, use a reverse proxy.
To allow clients to acess Tamr securely over HTTPS, configure a reverse proxy server to:
- communicate over HTTPS between the client and the proxy.
- communicate over HTTP between the proxy and Tamr.
Tamr requires only one port to be reachable from the client. By default this port is 9100.
For a list of additional ports that Tamr and its dependencies use, see Included Services and Ports. These ports are used for internal communications and do not need to be served to the client.
Example: Configuring a Reverse Proxy
Use the NGINX application server to configure a reverse proxy.
This example configures a reverse proxy to allow secure access to Tamr over HTTPS.
The example:
- uses the NGINX application server as a reverse proxy.
- establishes a proxy between the default Tamr port
9100onhttpand port443onhttps.
Installing NGINX on RHEL 7
- Update the repository information.
sudo yum update
- Install the
nginxpackage.
sudo yum install nginx
- Enable automatic service start.
sudo systemctl enable nginx.service
Installing NGINX on Ubuntu
- Update the repository information.
sudo apt-get update
- Install the
nginxpackage.
sudo apt-get install nginx
Configuring an NGINX server proxy to allow secure access to Tamr over HTTPS
To configure an NGINX server proxy for HTTPS, we require:
- a signed certificate.
- the signed certificate's private key file and pass phrase.
- Copy the certificate and private key files,
.crtand.keyrespectively, into a directory, such as/etc/nginx/keys.
sudo mkdir /etc/nginx/keys
cd /etc/nginx/keys
sudo cp <signed-certificate>.crt .
sudo cp <signed-certificate-private-key>.key .
- Create a pass phrase file to store the private key's pass phrase.
cd /etc/nginx/keys
sudo vi global.pass
- In the NGINX configuration directory
/etc/nginx/conf.d, create the configuration filetamr.conf.
cd /etc/nginx/conf.d
vi tamr.conf
- In the
tamr.conffile, add the following configuration.
server {
# Full path to the file containing the PEM pass phrase.
ssl_password_file /etc/nginx/keys/global.pass;
# SSL configuration
listen 443 ssl default_server;
listen [::]:443 ssl default_server;
root /var/www/html;
# Add index.php to the list if you are using PHP
index index.html index.htm index.nginx-debian.html;
server_name _;
ssl_certificate /etc/nginx/keys/<signed-certificate>.crt;
ssl_certificate_key /etc/nginx/keys/<signed-certificate-private-key>.key;
ssl_session_cache builtin:1000 shared:SSL:10m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4;
ssl_prefer_server_ciphers on;
location / {
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_pass http://localhost:9100;
proxy_read_timeout 90;
proxy_redirect http://localhost:9100 https://localhost:443;
}
}
NGINX default limit for uploading files
The default file size limit for uploading files through NGINX is 1MB.Therefore, you will be able to only upload files to Tamr via HTTPS that are up to 1MB in size. Note, this does not apply to clients uploading files via HTTP, such as clients acting locally on the Tamr server. To remove this limit, additionally configure
client_max_body_sizeto0.
- Restart the NGINX service.
sudo systemctl restart nginx.service
- Confirm that Tamr is now available by browsing directly to
https://<hostname>:443, such ashttps://tamr.<mydomain>.com.
Updated over 5 years ago